Top Qs
Timeline
Chat
Perspective
Key encapsulation mechanism
Public-key cryptosystem From Wikipedia, the free encyclopedia
Remove ads
In cryptography, a key encapsulation mechanism (KEM) is a public-key cryptosystem that allows a sender to generate a short secret key and transmit it to a receiver confidentially, in spite of eavesdropping and intercepting adversaries.[1][2][3] Modern standards for public-key encryption of arbitrary messages are usually based on KEMs.[4][5]

A KEM allows a sender who knows a public key to simultaneously generate a short random secret key and an encapsulation or ciphertext of the secret key by the KEM's encapsulation algorithm. The receiver who knows the private key corresponding to the public key can recover the same random secret key from the encapsulation by the KEM's decapsulation algorithm.[1][2][3]
The security goal of a KEM is to prevent anyone who does not know the private key from recovering any information about the encapsulated secret keys, even after eavesdropping or submitting other encapsulations to the receiver to study how the receiver reacts.[1][2][3]
Remove ads
Difference from public-key encryption
Summarize
Perspective

The difference between a public-key encryption scheme and a KEM is that a public-key encryption scheme allows a sender to choose an arbitrary message from some space of possible messages, while a KEM chooses a short secret key at random for the sender.[1][2][3]
The sender may take the random secret key produced by a KEM and use it as a symmetric key for an authenticated cipher whose ciphertext is sent alongside the encapsulation to the receiver. This serves to compose a public-key encryption scheme out of a KEM and a symmetric-key authenticated cipher in a hybrid cryptosystem.[1][2][3][5]
Most public-key encryption schemes such as RSAES-PKCS1-v1_5, RSAES-OAEP, and Elgamal encryption are limited to small messages[6][7] and are almost always used to encrypt a short random secret key in a hybrid cryptosystem anyway.[8][9][5] And although a public-key encryption scheme can conversely be converted to a KEM by choosing a random secret key and encrypting it as a message, it is easier to design and analyze a secure KEM than to design a secure public-key encryption scheme as a basis. So most modern public-key encryption schemes are based on KEMs rather than the other way around.[10][5]
Remove ads
Definition
Summarize
Perspective
Syntax
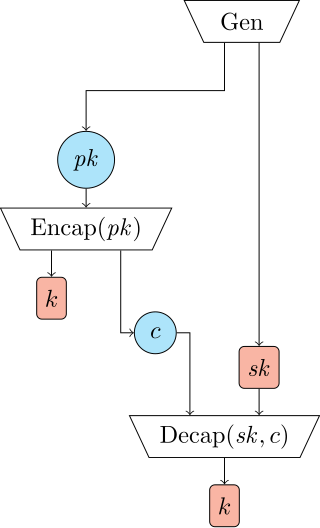
A KEM consists of three algorithms:[1][2][3][11][12]
- Key generation, , takes no inputs and returns a pair of a public key and a private key .
- Encapsulation, , takes a public key , randomly chooses a secret key , and returns along with its encapsulation .
- Decapsulation, , takes a private key and an encapsulation , and either returns an encapsulated secret key or fails, sometimes denoted by returning (called "bottom").
In the asymptotic setting of theoretical cryptography, the algorithms are all probabilistic polynomial-time in a security parameter , and the length of the secret key is a function of the security parameter .[1][2]
In practical cryptography, the secret key is usually of a fixed length for each algorithm. For example, ML-KEM always uses 256-bit secret keys,[4]: § 3.3, p. 16 while the algorithms in RFC 9180 vary between 256-, 384-, and 512-bit secret keys;[5]: § 7.1 secret keys of arbitrary length can be derived from by a key derivation function.[13]: § 5.3 [5]
Explicit vs. implicit rejection
Decapsulation can fail because its input is not an encapsulation returned by Encap, but has been tampered with or maliciously crafted. KEMs which report failure by a distinguished symbol (implemented in practice by returning an error code or raising an exception) are said to use explicit rejection. A KEM may instead return a random secret key in this event, or a secret key derived pseudorandomly from under the key ; this is called implicit rejection.[14]: § 5.3, pp. 76–78 [12]
Correctness
A KEM is correct if, for any key pair generated by , decapsulating an encapsulation returned by with high probability yields the same key , that is, .[2][3][11][12]
Security: IND-CCA
Security of a KEM is quantified by its indistinguishability against adaptive chosen-ciphertext attack, IND-CCA, which is loosely how much better an adversary can do than a coin toss to tell whether, given a random key and an encapsulation, the key is encapsulated by that encapsulation or is an independent random key.[2][3][11][12][1]
Specifically, in the IND-CCA game:
- The key generation algorithm is run to generate .
- is revealed to the adversary.
- The adversary can query for arbitrary encapsulations of the adversary's choice.
- The encapsulation algorithm is run to randomly generate a secret key and encapsulation , and another secret key is generated independently at random.
- A fair coin is tossed, giving an outcome .
- The pair is revealed to the adversary.
- The adversary can again query for arbitrary encapsulations of the adversary's choice, except for .
- The adversary returns a guess , and wins the game if .
The IND-CCA advantage of the adversary is , that is, the probability beyond a fair coin toss at correctly distinguishing an encapsulated key from an independently randomly chosen key.
Remove ads
Applications
Summarize
Perspective
Public-key encryption
A key encapsulation mechanism can be used together with an authenticated symmetric cipher to construct a public-key encryption scheme for arbitrary messages. The security requirement for the symmetric cipher, called a data encapsulation mechanism or DEM, is indistinguishability against chosen-ciphertext attack for a single message encrypted by the sender.[15][11][16]
Given a secure KEM with algorithms Gen/Encap/Decap, and a secure DEM , the following hybrid public-key encryption scheme is also secure against adaptive chosen-ciphertext attack in the public-key setting:[1][2]: § 7.2, Theorem 7.3 [13]: § 6.2.1
- Key generation: Same as the KEM.
- To encrypt a message for a public key :
- Let .
- Let .
- Send as the ciphertext.
- To decrypt a ciphertext with private key :
- Let , or fail if it fails.
- Return the message , or fail if it fails.
Note that—as with any public-key encryption on its own—this does not authenticate the sender: anyone with the public key can send a message to a recipient with the private key. Other cryptography, such as digital signatures, must be used in a protocol for a sender to prove its identity to the receiver.[17]
The use of an authenticated symmetric cipher is nevertheless required in this anonymous public-key encryption scheme to meet IND-CCA security. If an unauthenticated cipher were used, secure only against chosen-plaintext attack (IND-CPA), an adversary could selectively modify a message through its ciphertext in transit, which not only fails IND-CCA on a technicality[18] but also can compromise confidentiality in practice as in EFAIL.[19]
Key agreement protocols
A KEM can also be used in an authenticated key agreement protocol such as TLS with forward secrecy for an online session, by having the client and server generate KEM key pairs and exchange signed encapsulations using those key pairs, which they then erase at the end of the session.[13]
Combining KEMs
Different KEMs rely on different mathematical problems for their security. For example, the security of Rabin-KEM relies on the difficulty of integer factorization,[11] which has been studied for centuries, but is known to be vulnerable to quantum computers capable of running Shor's algorithm. In contrast, the security of ML-KEM relies on the difficulty of learning with errors,[4] which has only been studied for decades, but is not known to be vulnerable even to an adversary with a Shor-capable quantum computer.
A KEM combiner is a scheme for combining two KEMs, KEM1 and KEM2 with respective encapsulation algorithms KEM1.Encap and KEM2.Encap and so on, into a combined KEM which is secure if either KEM1 or KEM2 is secure.[20]
A KEM that combines a quantum-vulnerable KEM such as DH-KEM using X25519 with a post-quantum KEM such as ML-KEM is sometimes called a hybrid,[21][10][22] not to be confused with a hybrid cryptosystem which combines public-key cryptography with symmetric-key cryptography.
Remove ads
Examples and motivation
Summarize
Perspective
RSA
Traditional RSA encryption, with -bit moduli and exponent , is defined as follows:[23][24][25]
- Key generation, :
- Generate a -bit semiprime with at random satisfying , where is the Carmichael function.
- Compute .
- Return as the public key and as the private key. (Many variations on key generation algorithms and private key formats are available.[26])
- Encryption of -bit message to public key , giving :
- Encode the bit string as an integer with .
- Return .
- Decryption of ciphertext with private key , giving :
- Compute .
- Decode the integer as a bit string .
This naive approach is totally insecure.
For example, since it is nonrandomized, it cannot be secure against even known-plaintext attack—an adversary can tell whether the sender is sending the message ATTACK AT DAWN versus the message ATTACK AT DUSK simply by encrypting those messages and comparing the ciphertext.
Even if is always a random secret key, such as a 256-bit AES key, when is chosen to optimize efficiency as , the message can be computed from the ciphertext simply by taking real number cube roots, and there are many other attacks against plain RSA.[23][24] Various randomized padding schemes have been devised in attempts—sometimes failed, like RSAES-PKCS1-v1_5[23][27][28]—to make it secure for arbitrary short messages .[23][24]
Since the message is almost always a short secret key for a symmetric-key authenticated cipher used to encrypt an arbitrary bit string message, a simpler approach called RSA-KEM is to choose an element of at random and use that to derive a secret key using a key derivation function , roughly as follows:[15][8][16]
- Key generation: As above.
- Encapsulation for a public key , giving :
- Choose an integer with uniformly at random.
- Return and as its encapsulation.
- Decapsulation of with private key , giving :
- Compute .
- Return .
This approach is simpler to implement, and provides a tighter reduction to the RSA problem, than padding schemes like RSAES-OAEP.[15]
Elgamal
Traditional Elgamal encryption is defined over a multiplicative subgroup of the finite field with generator of order as follows:[29][30]
- Key generation, :
- Choose uniformly at random.
- Compute .
- Return as the private key and as the public key.
- Encryption of a message to public key , giving :
- Choose uniformly at random.
- Compute:
- Return the ciphertext .
- Decryption of a ciphertext for a private key , giving :
- Fail and return if or if , i.e., if or is not in the subgroup generated by .
- Compute .
- Return .
This meets the syntax of a public-key encryption scheme, restricted to messages in the space (which limits it to message of a few hundred bytes for typical values of ). By validating ciphertexts in decryption, it avoids leaking bits of the private key through maliciously chosen ciphertexts outside the group generated by .
However, this fails to achieve indistinguishability against chosen-ciphertext attack. For example, an adversary having a ciphertext for an unknown message can trivially decrypt it by querying the decryption oracle for the distinct ciphertext , yielding the related plaintext , from which can be recovered by .[29]
Traditional Elgamal encryption can be adapted to the elliptic-curve setting, but it requires some way to reversibly encode messages as points on the curve, which is less trivial than encoding messages as integers mod .[31]
Since the message is almost always a short secret key for a symmetric-key authenticated cipher used to encrypt an arbitrary bit string message, a simpler approach—called Elgamal-KEM or DH-KEM—is to derive the secret key from and dispense with and altogether, as a KEM, using a key derivation function :[1][5]
- Key generation: As above.
- Encapsulation for a public key , giving :
- Choose uniformly at random.
- Compute .
- Return and as its encapsulation.
- Decapsulation of with private key , giving :
- Fail and return if , i.e., if is not in the subgroup generated by .
- Compute .
- Return .
When combined with an authenticated cipher to encrypt arbitrary bit string messages, the combination is essentially the Integrated Encryption Scheme. Since this KEM only requires a one-way key derivation function to hash random elements of the group it is defined over, in this case, and not a reversible encoding of messages, it is easy to extend to more compact and efficient elliptic curve groups for the same security, as in the ECIES, Elliptic Curve Integrated Encryption Scheme, or RFC 9180 DHKEM(...) instances.
Remove ads
See also
References
Wikiwand - on
Seamless Wikipedia browsing. On steroids.
Remove ads
























![{\displaystyle \left|\Pr[b'=b]-1/2\right|}](http://wikimedia.org/api/rest_v1/media/math/render/svg/f6bca587c4ff5305de69acbb9ae92751cbb59a26)































































